Modern workplaces face a complex operational challenge daily. They must securely manage numerous types of visitors in a company, and this is a core security and control function, not simple hospitality.
Organizations host diverse individuals with different needs and risks. One common approach does not suit all these different needs, that’s why proper control, depending on office visitors and their purposes, begins with understanding.
Safety and efficiency depend on proper classification. It, in turn, assigns access levels and determines compliance procedures. A visitor identification in the office converts haphazard handling into a systematic process. A visitor management system brings in these categories without any hassle by connecting each visitor type to specific digital workflows.
Contents
- 1 Why Understanding Visitor Types Is Essential for Modern Visitor Management
- 2 Types of Visitors in a Company: A System-Based Classification
- 3 How Visitor Management Systems Identify and Handle Different Visitor Types
- 4 Visitor Types, Risk Levels, and Workplace Security
- 5 How Visitor Types Impact Compliance, Records, and Audits
- 6 Visitor Logs and Digital Records by Visitor Type
- 7 How Visitor Management Systems Support Visitor Experience Across All Visitor Types
- 8 Choosing Visitor Management Software That Supports All Visitor Types
- 9 Conclusion
- 10 FAQs: Types of Visitors in A Company
- 10.1 What are the different types of visitors in a company?
- 10.2 Why is identifying visitor types important for workplace security?
- 10.3 How does a visitor management system handle different visitor types?
- 10.4 What is the difference between low-risk and high-risk visitor types?
- 10.5 How do visitor types affect access permissions in an office?
- 10.6 How does visitor classification support compliance and audits?
- 10.7 What information is collected during visitor check-in for different visitor types?
- 10.8 How does visitor management improve the visitor experience?
- 10.9 What should organizations look for in visitor management software?
Why Understanding Visitor Types Is Essential for Modern Visitor Management
Businesses cannot manage what they do not first categorize and understand. A single sign-in sheet treats everyone the same. This creates significant security gaps and operational inefficiencies immediately.
Different visitor types in an organization pose different inherent risks. For instance, a delivery person and a financial auditor require distinct oversight. Proper visitor management aligns control levels with individual visitor purposes.
Knowing who is in your building is a basic safety requirement. Categorization links each person to a host and a clear purpose, as it establishes immediate accountability for every office visitor on site.
Receptionists cannot make consistent, real-time security decisions alone. That said, a predefined system for visitor management software guides their actions. This ensures uniform handling based on policy, not personal judgment.
Align your visitor strategy with operational risk, not reception habits. ➡ Visit www.othership.com
Types of Visitors in a Company: A System-Based Classification
Effective systems classify types of visitors in a company by purpose and origin. This logical grouping informs every subsequent workflow step. Moreover, it is the critical first input for any visitor management system.
Groups are defined by their need for access and level of risk. This moves beyond a simple list of who your visitors are. It treats visitor diversity as a fundamental system design issue.

Every category follows a tailored digital pathway, just to ensure both security compliance and operational efficiency. Understanding types of visitors in an office is the cornerstone of this process.
Internal Visitor Types Within a Company
Staff who change their locations between departments or sites are considered to be internal visitors. Still, they need a presence in the visitor management system to make office security possible. The monitoring of this movement helps to protect the assets and make the evacuations safe in case of an emergency.
A centralized system recognizes these professionals as authorized visitors with specific, temporary access needs. It ensures they can navigate necessary areas without obstruction. This prevents workflow friction while upholding consistent security protocols organization-wide.
External Visitor Types Entering the Workplace
Typically, visitors from outside of the company who come to an office consist of business guests such as clients or partners. On the other hand, contractors and delivery personnel are considered to be service providers, which is another large group. Job seekers and regulation inspectors make up another unique group that has specific needs.
The business ecosystem is dependent on a constant flow of external partners and specialists. Each type of external visitor entering the workplace has a specific purpose, for example, from meetings with clients to servicing of the equipment. Their different needs require a management approach that is both structured and flexible from the very moment they arrive.
To the visitors, the streamlined process is immediately a sign of professionalism and respect for their time. Simple, category-specific check-ins for these office visitors reduce front-desk congestion efficiently. This operational clarity allows guests to focus on their core business with the company.
Map external visitor purposes before designing visitor workflows, using insights from platforms like Othership.
How Visitor Management Systems Identify and Handle Different Visitor Types
A robust visitor management system uses categories to trigger specific workflows. Upon identification, the software applies predefined rules instantly. This automates the differentiation and routing of each office visitor.

The visitor management software treats type as a key data point. This determines the check-in method and required approvals automatically. The visitor registration experience adapts to the individual seamlessly.
This logic applies to data collection, notifications, and access permissions. The system allows high-risk visitors to be subjected to strict protocols. The visitor management software handles this complicated routing in an easy and dependable way.
Visitor Check-In and Registration by Visitor Type
Different types of visitors have their own data captured during the visitor registration process. A contractor may need to present a certificate of insurance digitally. A guest might simply confirm a pre-approved meeting time instantly.
A one-size-fits-all check-in frustrates both guests and reception staff. That’s the reason why visitor check-in and registration should adapt intelligently to each visitor category. A client may simply confirm a pre-scheduled appointment quickly, while a contractor might need to digitally sign safety waivers first.
A tailored approach streamlines the entry process for everyone involved, and captures all necessary compliance data without unnecessary questions as well. Efficient visitor registration respects the visitor’s time and your operational requirements simultaneously. The system ensures no critical step is ever missed.
Access Permissions and Approvals Based on Visitor Category
Access rights are automatically linked to visitor types within the software. A lunchtime visitor might be electronically issued a badge valid only for the lobby area, while an accorded supplier is allowed to use the elevator to go to a certain floor for a limited time.
Visitor badges should reflect clear, logical access rights aligned to their purpose. The classification of visitors automatically enforces the principle regarding access permissions and approvals. For instance, a person who delivers gets a security card only for the loading dock. Or an auditor of financial records acquires a pass for limited access to departments only for a certain period of time.
The implementation of automation in this process makes your security position clear-cut and uniform. Whenever a visitor stays, the system immediately assigns the right access. It also revokes all permissions automatically at the visit’s conclusion, which then creates a secure, self-expiring access environment for all guests.
Visitor Types, Risk Levels, and Workplace Security
The visitors that come to a business do not all bring the same level of security risks. Visitor management must be proportional, balancing safety with operational flow. A risk-based approach applies appropriate controls to each category intelligently.
Factors include access scope, visit duration, and area sensitivity. A one-time delivery poses a different risk than a long-term IT contractor. Modern visitor management system protocols account for these variables precisely.
This analytical approach prevents unnecessary friction for low-risk guests. It also ensures heightened scrutiny where it is genuinely warranted. Protecting assets requires this nuanced understanding of office visitors.
Low-Risk vs High-Risk Visitor Types
Not every guest requires the same level of security scrutiny. Distinguishing between low-risk and high-risk visitor types prevents unnecessary operational friction. A familiar client partner presents a very different profile from an unfamiliar service technician. Your protocols should reflect this practical reality accurately.
A standard business guest is typically a low-risk visitor. On the other hand, a technician doing maintenance on secure servers might be a risky office visitor. The distinction guides the depth of screening and level of escort required.
High-risk categorization is not based on suspicion but rather on the scope of access and the length of the visit. An IT contractor who works long-term needs to be vetted more extensively than a guest who is invited for lunch. The effective systems impose stronger controls for these visitor categories without notifying them. This way of managing the situation protects the assets and does not create a fortress mentality at the same time.
How Visitor Types Impact Compliance, Records, and Audits
Each visitor type has a different impact on compliance records in an organization. A visitor management system must maintain accurate, searchable logs for each category. This digital paper trail is essential for accountability and audit responses.
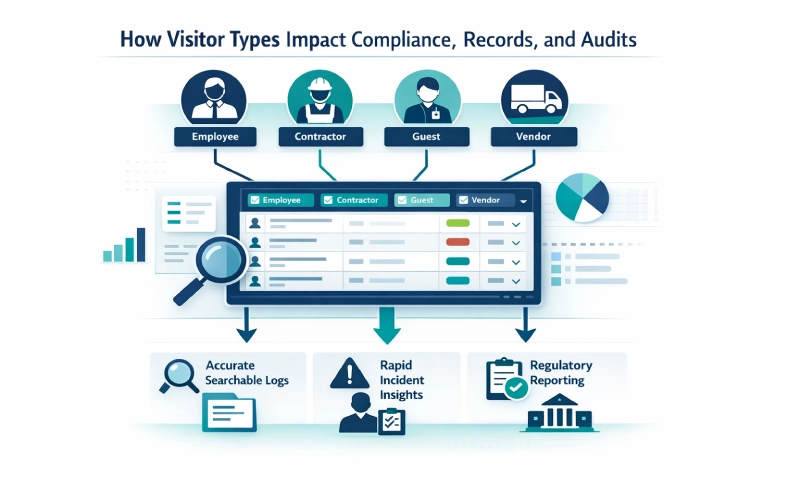
During an incident, it is imperative to rapidly determine the identity of all persons present. The logs arranged by categories allow instant filtering according to the type of visitor and their position. This feature helps the investigators to get the noisy data as intelligible information.
There are laws most of the time that require keeping certain records for contractor hours or site access. A system that tags entries by visitor type simplifies this reporting. Visitor registration data becomes a robust compliance asset effortlessly.
Visitor Logs and Digital Records by Visitor Type
Digital logs automatically associate data with a visitor category. This, in turn, guarantees uniformity among all the instances of visitor registrations. The best visitor management software uses this to generate reports on vendor frequency or client visits.
A paper logbook fails to provide actionable insights during a critical review. Modern visitor logs and digital records by visitor type transform raw data into intelligence. You can instantly filter records to see all contractor activity from last week. This capability turns compliance from an archival task into a strategic asset.
These categorized records provide clarity for internal audits and liability investigations. They definitely show who accessed which area and for how long. Maintaining pristine visitor registration history protects your organization and its people. It offers a clear, defensible narrative of all onsite activity.
How Visitor Management Systems Support Visitor Experience Across All Visitor Types
A smooth experience stems from clarity and efficiency, not just warmth. A visitor management system provides clear instructions tailored to each visitor type. This reduces uncertainty and creates a professional, welcoming impression immediately.
Confusion at reception creates frustration for guests and staff alike. Streamlined, type-specific workflows prevent this friction at the point of entry. Welcoming visitors to a company is about demonstrating respect for their time.
The system handles administrative tasks silently and quickly. The employees get more time to make valuable human connections. The reception of visitors turns into a real interaction, not an obstacle in the course of the procedures.
Reception Workflows and Greeting Visitors Consistently
Every guest gets the same quick procedure thanks to the organized workflows. The receptionist who welcomes the visitors sticks to an unambiguous, system-guided protocol. That is why professional and uniform first impressions are created for all the categories of guests.
The reception area sets the tone for every professional relationship. Standardized reception workflows and greeting visitors consistently ensure a flawless first impression. Every guest, from a CEO to a courier, receives the same efficient, guided process. The established credibility provides instant trust and a positive image for the whole of your organization.
A well-defined process gives your front-desk personnel assurance and transparency.. The process of welcoming guests will be so smooth that the friendliness of the staff will not be affected by any delays from following the procedures. The coexistence of modernity, efficiency, and the ability to attract more people to a workplace that is open and friendly is still commonly seen in today’s corporate environment.
Choosing Visitor Management Software That Supports All Visitor Types
Select software that mirrors your organization’s complexity in visitor categories. The visitor management software must map to your real-world classification needs. Evaluate its flexibility to generate and direct various types of customers.
The mechanism should be entirely competent in applying distinct regulations for every party you choose. It should be able to handle low-risk customers and high-risk workers in a similar manner. The right software for visitor management becomes an extension of your security policy.
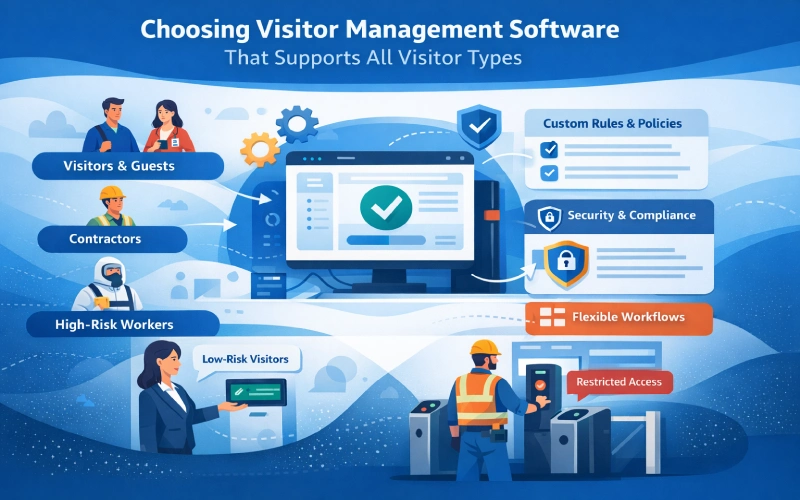
Avoid solutions that offer only a one-size-fits-all visitor process. Your chosen platform should grow and adapt as your visitor demographics evolve. With that said, prioritize a visitor management system built on the principle of intelligent categorization.
Conclusion
Managing types of visitors in a company requires a systemic, not situational, approach. Classification is the essential first step that informs every subsequent security and operational action. A contemporary visitor management system smoothly executes this logic.
By understanding visitor types in an office, businesses implement proportional, risk-aware controls. This protects people, assets, and data while maintaining a professional flow.
The journey begins with moving beyond a simple list of who your visitors are. It culminates in a fully integrated, intelligent workflow. Investing in capable visitor management software is the definitive step to achieve this operational maturity.
Design visitor management around systems—not reception desks—using platforms like Othership.
FAQs: Types of Visitors in A Company
What are the different types of visitors in a company?
Types of visitors in a company generally include internal visitors (employees moving between sites or departments) and external visitors such as clients, partners, contractors, service providers, delivery personnel, job candidates, and auditors. Each category has different access needs and risk levels.
Why is identifying visitor types important for workplace security?
Identifying visitor types allows organizations to assign appropriate access levels, apply relevant security controls, and maintain accountability. Treating all visitors the same creates security gaps and operational inefficiencies.
How does a visitor management system handle different visitor types?
A visitor management system categorizes visitors at check-in and automatically triggers predefined workflows. These workflows control data collection, approvals, notifications, access permissions, and badge validity based on visitor type.
What is the difference between low-risk and high-risk visitor types?
Low-risk visitors typically include short-term business guests with limited access needs, while high-risk visitors may include contractors or technicians requiring extended access to sensitive areas. Risk is determined by access scope, visit duration, and area sensitivity.
How do visitor types affect access permissions in an office?
Access permissions are assigned based on visitor category. For example, a delivery visitor may only access loading areas, while a contractor may receive time-bound access to specific floors. Permissions are automatically revoked when the visit ends.
How does visitor classification support compliance and audits?
Visitor classification ensures accurate digital records for each visitor type. These categorized logs simplify audits, incident investigations, and regulatory reporting by providing clear visibility into who was onsite, where they accessed, and for how long.
What information is collected during visitor check-in for different visitor types?
The data collected during visitor registration varies by visitor type. Guests may only confirm meeting details, while contractors may need to submit certifications, sign waivers, or complete additional compliance steps digitally.
How does visitor management improve the visitor experience?
Visitor management systems streamline check-in with clear, type-specific instructions. This reduces wait times, eliminates confusion at reception, and creates a consistent, professional experience for all office visitors.
What should organizations look for in visitor management software?
Organizations should choose visitor management software that supports multiple visitor types, allows flexible workflow configuration, enforces risk-based access controls, and maintains accurate, searchable visitor records.




You must be logged in to post a comment.