The visitor management process defines how organizations receive, identify, and control workplace visitors. It creates accountability by documenting who enters, where they go, and when they leave.
This visitor management procedure protects employees, assets, and operations from unnecessary risk. Modern workplaces rely on visitor management to maintain order, safety, and compliance.
Contents
- 1 What Is the Visitor Management Process?
- 2 Why Visitor Management Is Important in the Workplace
- 3 Types of Visitors in a Company
- 4 Key Steps in the Visitor Management Process
- 5 Visitor Management Guidelines and Security Policies
- 6 Challenges of Manual Visitor Reception and Tracking
- 7 How Visitor Management Software Improves the Process
- 8 Core Features of a Visitor Management System
- 9 Building Visitor Management Systems vs Using Ready Solutions
- 10 Office Visitor Management Systems and Access Control
- 11 How Othership Supports the Visitor Management Process
- 12 When to Upgrade Your Visitor Management Process
- 13 Improve Your Visitor Management Process with Othership
- 14 Visitor Management Process – FAQ Questions
- 14.1 1. What is the visitor management process in a workplace?
- 14.2 2. Why is visitor management important for office security and compliance?
- 14.3 3. What are the main steps in a visitor management process?
- 14.4 4. How does visitor check-in work in a modern visitor management system?
- 14.5 5. What types of visitors should be included in a visitor management procedure?
- 14.6 6. What is the difference between visitor management and a visitor management system (VMS)?
- 14.7 7. How does visitor management software improve visitor security and tracking?
- 14.8 8. When should a company upgrade its visitor management process?
What Is the Visitor Management Process?
The visitor management system is a formalized process for dealing with external visitors. It regulates entry, identification, supervision, and exit using a consistent method across the workplace. This effective visitor control replaces informal reception practices with structured procedures.

A well-designed visitor management process combines security, compliance, and productivity. It does not disrupt daily operations. Instead of removing informal decisions, it standardizes actions to reduce risk and human error. This approach enforces rules for all departments and locations.
The visitor management process reinforces duty of care and accountability from the HR and leadership perspective. It guarantees visitors receive necessary access while employees are protected from disturbances. Efficient visitor management demonstrates governance maturity and builds trust with stakeholders.
Definition of Visitor Management
The definition of visitor management is determined by visibility, access rights, and responsibility. This explains what visitor management is without referencing specific tools or vendors. The process prioritizes control over convenience.
Visitor Management Process vs Visitor Management System
The visitor management process sets the rules, policies, and workflows governing all visits. A visitor management system (VMS) is the software or solution that applies these rules digitally, handling the ‘how’ of each step. The process addresses what should be done, while the system ensures those actions are efficiently carried out.
Why Visitor Management Is Important in the Workplace
The significance of visitor management can be understood through the primary lens of risk mitigation. Not having visitors logged in or monitored presents various threats, including safety, compliance, and damage to the organization’s reputation. A robust visitor security system not only ensures the safety of the employees but also of the sensitive environments, such as labs, R&D, etc.
Visitor management is thus a key factor for organizations to maintain their operations without interruptions. Strong visitor management helps meet regulatory and internal standards. It creates reliable records for auditing incidents. This transparency allows firms to show diligence and responsibility for operations.
Moreover, effective visitor management maintains productivity and culture. Clear procedures prevent confusion, delays, and disruptions, while consistent practices build trust, order, and confidence for business leaders.
Improving Visitor Security and Access Control
Visitor security starts with verified identification. A systematic access management method blocks unauthorized people. With this, controlled entry helps prevent theft, data leaks, and accidents. High-tech control prepares emergency teams.
Enhancing Visitor Experience and First Impressions
Strong visitor experience management makes operations efficient and secure. Clear reception workflows reduce confusion and wait times. Thus, a smooth and predictable process gives visitors a pleasant feeling, and professional entry leaves a strong impression.
Types of Visitors in a Company
Not all visitors are the same, and treating them that way can create risk and slow teams down. A good reception tailors its approach to why someone is visiting and for how long, which makes smarter security decisions along the way.
Guests, Clients, and Interviewees
Guests and interviewees usually need only short-term access. Clear visitor workflows alert hosts right away and keep movement supervised, striking a natural balance between being welcoming and staying in control.
Vendors, Contractors, and Service Providers
Vendors require tighter identification since they often stay longer on site. Controlled entry zones and ongoing monitoring help reduce safety, compliance, and liability risks.
Key Steps in the Visitor Management Process
The visitor management process follows a logical sequence. Each step strengthens visibility and accountability. That’s why a defined visitor management procedure ensures consistent execution. Through this, organizations reduce errors through structured workflows.

Pre-Registration and Visitor Approval
Pre-registration helps security prepare before visitors arrive. Access needs are verified early, easing front-desk congestion and making visitor management smoother and more secure.
Visitor Check-In and Identification
Modern check-ins move beyond handwritten logs. Digital identification captures accurate data, improves traceability, and reduces errors at the front desk as well.
Host Notification and On-Site Monitoring
Hosts get instant notifications of arrivals. Active monitoring keeps visitors supervised. Prevent unauthorized movement easily. This only proves that effective controls support workplace safety.
Visitor Check-Out and Record Management
Exit logging closes the loop on every visit. Reliable tracking improves compliance reporting and provides trustworthy records to support audits and investigations.
Visitor Management Guidelines and Security Policies
Clear guidelines standardize workplace behavior. A written policy removes confusion. And with consistent enforcement, visitor security surely strengthens. After all, policies keep teams aligned across locations.
Visitor Identification and Access Rules
Access rules vary by visitor type. A structured visitor identification system enforces authorization. The management of visitor access minimizes the risk of exposure. Rules protect people and assets.
Data Privacy and Visitor Records
Visitor data should always be handled with care. Secure tracking protects privacy, accurate monitoring supports audits, and clear retention policies help maintain compliance.
Challenges of Manual Visitor Reception and Tracking
Traditional manual reception relies heavily on human accuracy, while paper logs offer no real-time visibility. As visitor volumes grow, organizations quickly outgrow manual sign-in methods, and from here, increasing risk follows.
Security Gaps and Human Error
Paper logs fail during emergencies, and knowing that manual visitor monitoring offers no alerts, these errors weaken overall visitor security. As a result, real-time control becomes impossible.
Poor Visitor Experience and Delays
Manual processes slow visitor check-in, which then causes frustration to visitors and hosts. Weak visitor experience management harms professionalism, while productivity suffers across teams.
How Visitor Management Software Improves the Process
Visitor management software automates critical workflows, which reduces errors and delays. But with Modern visitor management solutions, visibility is improved and. organizations obtain consistent control.
Automating Visitor Check-In and Tracking
An automated visitor management system eliminates paper logs. Real-time tracking provides better control, and digital workflows increase accountability. Therefore, reception operates seamlessly.
Centralized Visitor Data and Reporting
Centralized dashboards make it easier to monitor visitors. The top management gets to know through a visitor management system. Reports are used in audits and planning, and with this, data leads to better choices being made.
Core Features of a Visitor Management System
The features of a visitor management system that work effectively will lead to good operational outcomes. Every visitor management tool corresponds to the process steps. Strong visitor software management ensures consistency. Features should reduce risk.
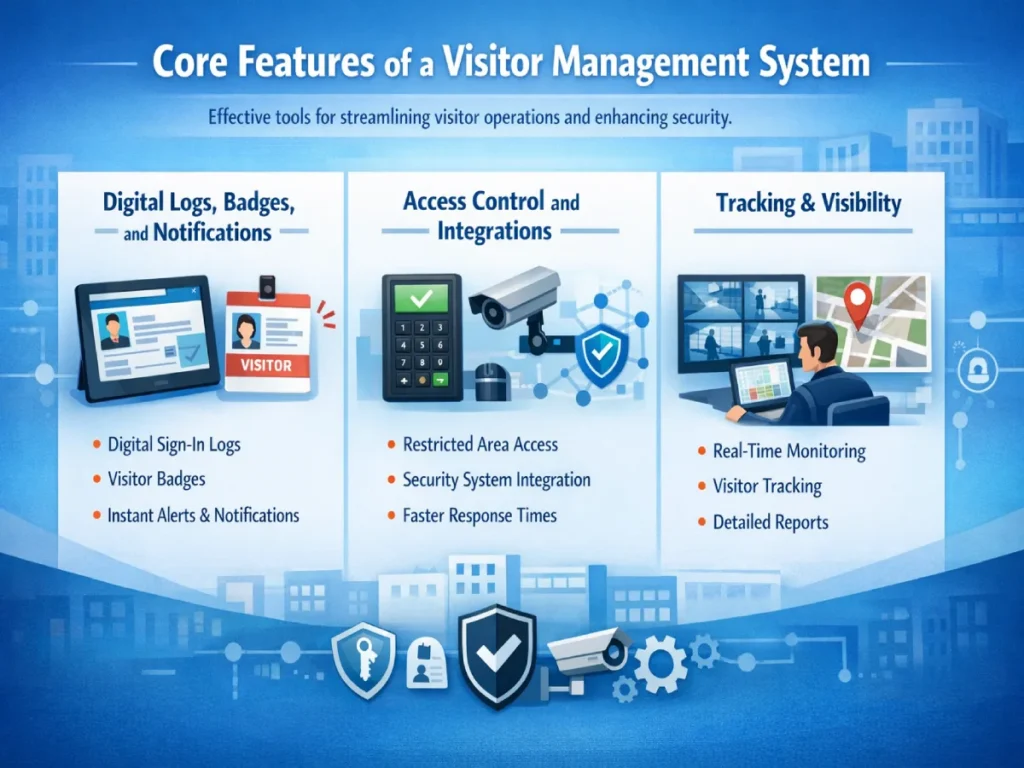
Digital Logs, Badges, and Notifications
Tools like digital sign-in logs, visitor badges, and real-time notifications streamline front-desk workflows. They improve visibility, keep staff informed, and ensure visitors are properly tracked throughout their stay.
Access Control and Integrations
A visitor access management system integrates with security tools. The visitor entry system restricts unauthorized areas. The integrated systems also lead to faster responses, so security teams gain visibility.
Building Visitor Management Systems vs Using Ready Solutions
Building custom systems adds ongoing maintenance and complexity. Ready-made visitor management solutions scale faster and help organizations save time, effort, and resources.
Implementation is sped up, and operational load is lightened with the use of prepared visitor management systems. These systems illustrate the risks that can occur in real workplaces in a way that has been tried out before through the use of established workflows. Business executives acquire instant organization without having to deal with technical intricacy.
From the standpoint of human resources and governance, the infrastructure of management systems for visitors to ready-made systems provides the scalability and policy uniformity. They are more quickly adjusted to the changes in the regulations and growth of the workforce. The selection of visitor management solutions that are already in place leads to rapid and less risky, more informed decision-making.
Office Visitor Management Systems and Access Control
An office visitor management system keeps daily operations running smoothly. Unified access management gives multi-location teams better visibility, while consistent workflows help reduce risk across offices.
Strong access control within an office visitor management system limits visitor movement to approved areas. This approach reduces exposure to sensitive information and restricted work zones. The HR and the security departments feel more certain of the access rules being uniformly and consistently applied.
An office visitor management system with integrated capabilities is the answer to multi-site offices and hybrid working situations. A single point of access control helps attain the same policies at all locations. The corporate executives are the ones who enjoy the strongest advantages in terms of their visibility, compliance alignment, and operational trust.
How Othership Supports the Visitor Management Process
Othership is in line with the visitor management process. The visitor management system (VMS) of Othership is there to support every step. The visitor management solutions mentioned make security tighter to enhance security.
Through its visitor management system, Othership strengthens visibility across the entire visitor lifecycle. Real-time records help HR and security teams respond quickly to exceptions or incidents. Such an explanation gives the businesses the courage to stay compliant.
Othership’s visitor management systems are flexible according to the size of the office, number of visitors, and the requirements of governance. They are facilitating uniform policy application throughout the entire organization, regardless of department or location. Therefore, the executives will get a visitor management approach that can easily be expanded and is reliable for the stability of operations in the long run.
When to Upgrade Your Visitor Management Process
Visitor volume increases operational risk. Outdated tools weaken the visitor management process. The compliance obligations become more and more severe. The most popular visitor management systems are essential for contemporary workplaces.
An outdated visitor management process struggles to support compliance and audit readiness. Incomplete records weaken investigations and regulatory confidence. The human resources managers replace old systems to regain control and the trustworthiness of the documents.
Business growth often demands a more scalable visitor management process. Multi-site offices and hybrid work increase access complexity. Modern visitor management upgrades support consistency, security, and long-term operational resilience.
Improve Your Visitor Management Process with Othership
Othership strengthens the best visitor management software effectiveness. Its office visitor management system supports scalability. Organizations gain visibility and control. As a result, confidence improves across teams.
With Othership, businesses maintain accurate visitor logs and meet regulatory requirements effortlessly. By utilizing digital records, the risks linked to information that is lost or incomplete are minimized. HR workers can check the visits immediately, and thus, there is an improvement in compliance and operational transparency.
Othership integrates with calendar systems, thus facilitating the scheduling of meetings and cutting down the waiting times for visitors. Employees are dedicated to their main activities, while visitors have a smooth experience. This proficiency not only enhances the company’s professional image and visitor satisfaction, but also the latter.
Visitor Management Process – FAQ Questions
1. What is the visitor management process in a workplace?
The visitor management process indicates the way organizations welcome, recognize, supervise, and let go of visitors. It provides a constant level of accountability and safety during every visit. This process acts as a buffer for both employees and equipment.
2. Why is visitor management important for office security and compliance?
Visitor management prevents unauthorized access. It supports audits, investigations, and regulatory requirements. Strong visitor security reduces workplace risk.
3. What are the main steps in a visitor management process?
The visitor management process includes pre-registration, check-in, monitoring, and check-out. Each step improves visibility. Together, they ensure accountability.
4. How does visitor check-in work in a modern visitor management system?
Modern visitor check-in captures digital records. A visitor identification system verifies identity. Hosts receive instant notifications.
5. What types of visitors should be included in a visitor management procedure?
All types of visitors in a company require tracking. This includes guests, vendors, and contractors. Processes adapt based on risk.
6. What is the difference between visitor management and a visitor management system (VMS)?
Visitor management defines rules and workflows. A visitor management system VMS executes them digitally. Both work together.
7. How does visitor management software improve visitor security and tracking?
Visitor management software provides real-time visibility. Visitor tracking software improves accountability. Security teams respond faster.
8. When should a company upgrade its visitor management process?
Companies should upgrade when risks increase. Manual tools signal inefficiency. Modern needs require scalable visitor management systems.




You must be logged in to post a comment.